1 Attackers used simple malware2 Security measures
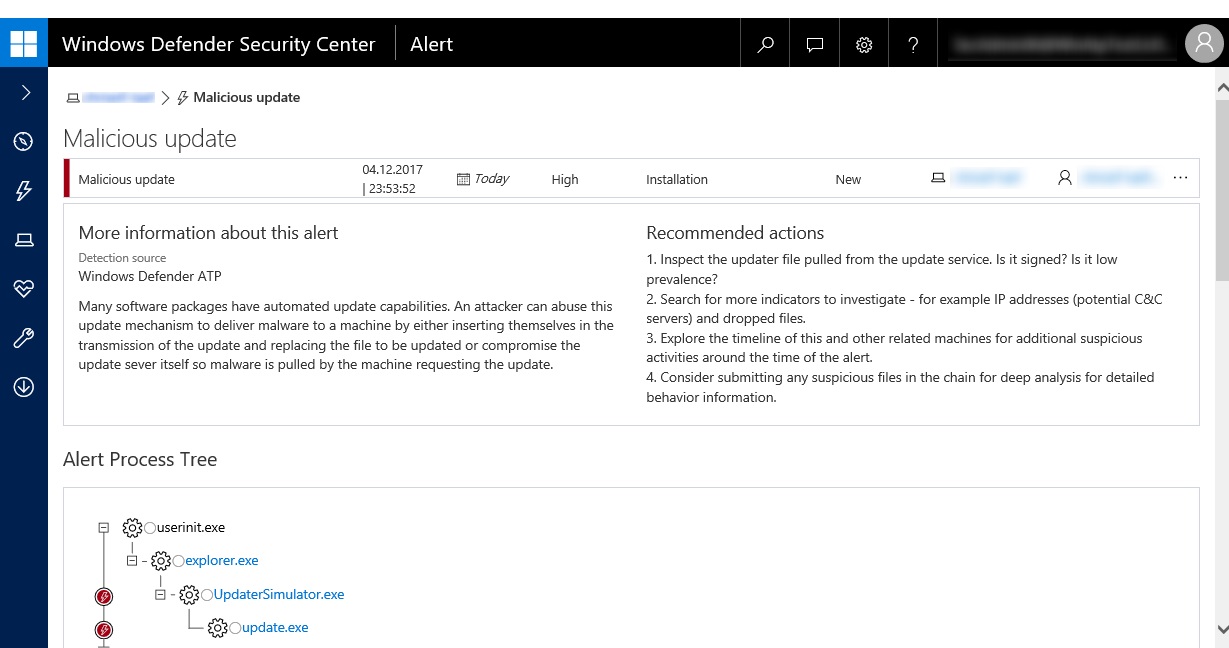
The company names the hacking campaign “WillySupply” and explains there could be a financial motivation behind it. According to Microsoft, the attackers used the updater of the editing software to deliver an “unsigned, low-prevalence executable”, then scanned the target’s network and established remote access. Microsoft notes that shortly after the attack, the Windows Defender Advanced Threat Protection (Windows Defender ATP) research team noticed the attack. Furthermore, the company explains that “this cyberattack could have been much more problematic if it had gone undetected.” Ultimately, Microsoft says that it was able to notify known affected parties who then contained the attempted attack and mitigated potential risks. A collaboration of security experts from the targeted industries and Microsoft researchers eventually neutralized the attack.
Attackers used simple malware
Another key point of this attempted attack are the tools that the hackers used. Microsoft notes that despite the fact that the attackers appear to have planned the attack carefully, they used commodity tools and simple malware. The Redmond giant explains that “these commodity tools used are the same tools used in typical penetration testing exercises.” Moreover, the malware binary -named ue.exe– was a small piece of code with the sole purpose of launching a Meterpreter shell. A Meterpreter shell is a common pen-test tool which the attackers downloaded using PowerShell.
Security measures
As a result, Microsoft warns software vendors about such attacks and provides a list of security measures for them. The company encourages vendors to provide automatic updaters using SDL best practices and instructs them to apply the following measures:
“Use strong encryption to protect update channels and to avoid being a target of attacks that use common pen-test tools like Evil Grade. Consider certificate pinning in the update protocol. Before running binaries downloaded from the update channel, always validate their digital signatures against your own certificates. Don’t allow blind execution. Place scripts and configuration files in signed containers. Unlike signed binaries, scripts and configuration files are often loaded unverified. Unless kept in signed containers, these files are prone to tampering. Be aware that clean, signed binaries might still allow malicious commands to be executed through the command-line. Likewise, web content used in the update process might allow execution of scripts when rendered. If your update process runs with higher privileges, don’t let it trust folders that can be modified with lower privileges such as the Temp folder. An updater process might inadvertently elevate privileges of arbitrary code that an attacker has placed in scripts, configuration files, or DLL files in these folders. Protect your update infrastructure from intrusion by applying regular security updates and getting critical mechanisms in place, such as a firewall, antimalware, 2FA authentication, and periodic log reviews.”